Since logical connections operate over physical links, the logical and physical architectures rely on each other, but the two also have a high degree of independence, as the physical configuration of a network can be changed without changing its logical architecture, and the same physical network can in many cases support different sets of standards and protocols.
The logical architecture of wireless networks will be described in this chapter with reference to the OSI model.
The OSI Network Model
The Open Systems Interconnect (OSI) model was developed by the International Standards Organisation (ISO) to provide a guideline for the development of standards for interconnecting computing devices. The OSI model is a framework for developing these standards rather than a standard itself — the task of networking is too complex to be handled by a single standard.
The OSI model breaks down device to device connection, or more correctly application to application connection, into seven so-called “layers” of logically related tasks (see Table 2-1). An example will show
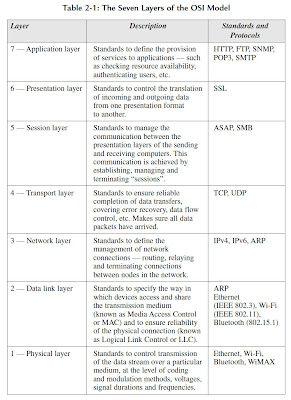
how these layers combine to achieve a task such as sending and receiving an e-mail between two computers on separate local area networks (LANs) that are connected via the Internet.
The process starts with the sender typing a message into a PC e-mail application (Figure 2-1). When the user selects “Send”, the operating system combines the message with a set of Application layer (Layer 7) instructions that will eventually be read and actioned by the corresponding operating system and application on the receiving computer.
The message plus Layer 7 instructions is then passed to the part of sender’s operating system that deals with Layer 6 presentation tasks. These include the translation of data between application layer formats as well as some types of security such as Secure Socket Layer (SSL) encryption. This process continues down through the successive software layers, with the message gathering additional instructions or control elements at each level.
By Layer 3 — the Network layer — the message will be broken down into a sequence of data packets, each carrying a source and destination
Wireless Network Physical Architecture
Wired Network Topologies — A Refresher
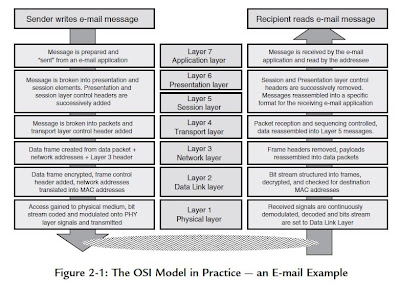
The topology of a wired network refers to the physical configuration of links between networked devices or nodes, where each node may be a computer, an end-user device such as a printer or scanner, or some other piece of network hardware such as a hub, switch or router.
The building block from which different topologies are constructed is the simple point-to-point wired link between two nodes, shown in Figure 3-1. Repeating this element results in the two simplest topologies for wired networks — bus and ring.
For the ring topology, there are two possible variants depending on whether the inter-node links are simplex (one-way) or duplex (two-way). In the simplex case, each inter-node link has a transmitter at one end and a receiver at the other, and messages circulate in one direction around the ring, while in the duplex case each link has both transmitter and receiver (a so-called transceiver) at each end, and messages can circulate in either
direction.
Bus and ring topologies are susceptible to single-point failures, where a single broken link can isolate sections of a bus network or halt all traffic in the case of a ring.
The step that opens up new possibilities is the introduction of specialised network hardware nodes designed to control the flow of data between
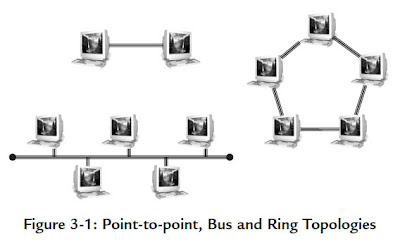 other networked devices. The simplest of these is the passive hub, which is the central connection point for LAN cabling in star and tree topologies, as shown in Figure 3-2. An active hub, also known as a repeater, is a variety of passive hub that also amplifies the data signal to improve signal strength over long network connections.
other networked devices. The simplest of these is the passive hub, which is the central connection point for LAN cabling in star and tree topologies, as shown in Figure 3-2. An active hub, also known as a repeater, is a variety of passive hub that also amplifies the data signal to improve signal strength over long network connections.For some PAN technologies, such as USB, star and tree topologies can be built without the need for specialised hardware,
 because of the daisy-chaining capability of individual devices (see Figure 2-11).
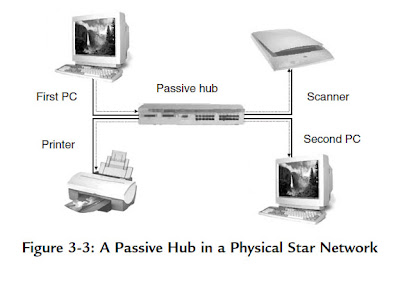
because of the daisy-chaining capability of individual devices (see Figure 2-11).An active or passive hub in a star topology LAN transmits every received data packet to every connected device. Each device checks every packet and decodes those identified by the device’s MAC address. The disadvantage of this arrangement is that the bandwidth of the network is shared among all devices, as shown in Figure 3-3. For example, if two PCs are connected through a 10 Mbps passive hub, each will have on average 5 Mbps of bandwidth available to it.
If the first PC is transmitting data, the hub relays the data packets on to all other devices in the network. Any other device on the network will have to wait its turn to transmit data.
A switching hub (or simply a switch) overcomes this bandwidth sharing limitation by only transmitting a data packet to the device to which it is addressed. Compared to a non-switching hub, this requires increased memory and processing capability, but results in a significant improvement in network capacity.
The first PC (Figure 3-4) is transmitting data stream A to the printer and the switch directs these data packets only to the addressed device. At the same time, the scanner is sending data stream B to the second PC.
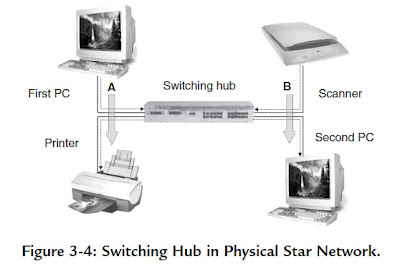
The switch is able to process both data stream concurrently, so that the full network bandwidth is available to every device.
Thank you for this fantastic resource...I really love reading your blog. I found it pleasant in google and I put on my list of favorites would like to see more posts from u soon.
ReplyDeletethanks man...
ReplyDeleteWhy it's necessary to use these color?
ReplyDeleteRespect and I have a super give: Where To Start Renovating House custom home renovations
ReplyDelete